Programmer
Website Programmers – Can AI Replace Them?
As Artificial Intelligence (AI) continues to advance, questions arise about its potential to revolutionize various industries, including web development. Website programmers play a pivotal role in creating functional and visually appealing websites. This article explores the potential impact of AI on website programming and whether it has the capability to replace human programmers.
1. Automated Code Generation
– AI-powered tools like code generators and auto-complete features are becoming more sophisticated. They can assist programmers by automating repetitive tasks and suggesting code snippets.
2. Template-Based Website Builders
– Website builders with AI capabilities allow users to create websites using pre-designed templates and intuitive interfaces. These tools significantly reduce the need for manual coding.
3. Natural Language Processing (NLP)
– NLP-powered platforms can interpret user instructions in plain language and generate corresponding code. This makes website development accessible to those with limited coding knowledge.
4. AI in Design and Layout
– AI-driven design tools can analyze user preferences and trends to generate aesthetically pleasing layouts. While not replacing programmers, it streamlines the design process.
5. Content Management Systems (CMS)
– Advanced CMS platforms employ AI for tasks like content categorization, SEO optimization, and personalized content recommendations, reducing manual intervention.
6. Debugging and Error Handling
– AI can identify and rectify common coding errors, enhancing the efficiency of the development process.
7. Performance Optimization
– AI algorithms can analyze website performance metrics and make real-time adjustments to enhance speed, responsiveness, and user experience.
8. Personalization and User Experience
– AI can analyze user behavior and preferences to dynamically adjust content and features, creating a personalized experience for each visitor.
9. Security Measures
– AI-powered security tools can detect and respond to potential threats, providing an added layer of protection for websites.
10. Complex Algorithm Development
– While AI can assist in creating algorithms, conceptualization and critical decision-making still require human expertise.
11. Ethical and Creative Decision-Making
– AI lacks the capacity for ethical considerations and creative ideation, which are crucial aspects of website development.
12. Adaptation to Unique Business Needs
– Human programmers understand the specific requirements and nuances of each project, allowing for tailored solutions that AI may struggle to replicate.
Conclusion
While AI has made remarkable strides in automating various aspects of website development, the role of website programmers remains indispensable. AI serves as a powerful tool to augment their capabilities, automate routine tasks, and enhance efficiency. However, the creativity, problem-solving, and nuanced decision-making that human programmers bring to the table are irreplaceable. As we move forward, a collaborative approach between AI and human programmers is likely to yield the most innovative and effective web development results.
What is CSS in Web Design? Are there different types of CSS?
CSS, which stands for Cascading Style Sheets, is a crucial component of web design. It is a stylesheet language that controls the presentation and layout of a webpage. Essentially, CSS dictates how HTML elements are displayed on a website, including aspects like color, font, spacing, and positioning.
Here are some key points about CSS in web design:
1. Styling and Presentation: CSS separates the content (provided by HTML) from its visual representation. It allows web designers to apply styles to elements, making them visually appealing and organized.
2. Selectors and Declarations: CSS uses selectors to target HTML elements and declarations to define how those elements should look. For example, you might use a selector to target all headings (`h1`, `h2`, etc.) and then declare that they should be displayed in a specific font and color.
3. Cascading Nature: The “Cascading” in CSS refers to how styles are applied. If multiple styles are defined for the same element, CSS follows a set of rules to determine which style takes precedence. This allows for flexibility and control in styling.
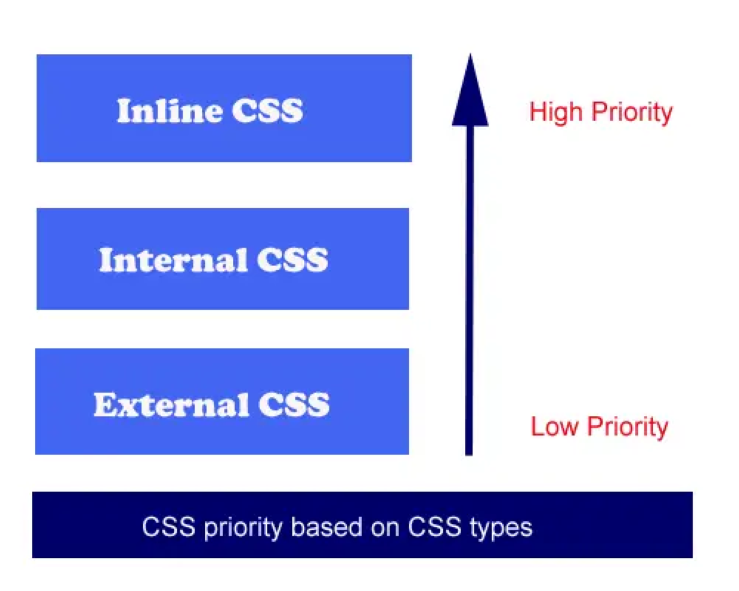
4. External, Internal, and Inline Styles: CSS can be implemented in different ways:
– External: A separate .css file is linked to the HTML document. This allows for easy management of styles across multiple pages.
– Internal: Styles are included within the HTML document using `<style>` tags in the `<head>` section. This is useful for single pages or when styles are specific to a particular page.
– Inline: Styles are applied directly to individual HTML elements using the `style` attribute. This method is less recommended due to its limited scalability and maintenance challenges.
5. Different Types of Selectors: CSS offers various types of selectors, including element selectors, class selectors, ID selectors, and more. Each type of selector allows for different levels of specificity and targeting.
6. Box Model: CSS uses a box model to define the space an element occupies. It includes properties like margin, border, padding, and content. Understanding the box model is crucial for layout design.
7. Flexbox and Grid: These are layout models in CSS that provide powerful tools for creating complex and responsive page layouts. They offer precise control over the arrangement of elements on a page.
8. Media Queries: CSS includes the capability to use media queries, allowing designers to apply different styles based on factors like screen size, device orientation, or resolution. This is crucial for creating responsive designs that adapt to various devices.
9. CSS Frameworks: These are pre-written, standardized CSS code that provide a foundation for building web pages. Popular CSS frameworks include Bootstrap, Foundation, and Bulma.
In summary, CSS is an essential tool in web design for controlling the look and feel of a webpage. Its capabilities extend to layout, color, typography, spacing, and more. Understanding CSS is fundamental for creating visually appealing and user-friendly websites.
Programming for SEOs
“Programming for SEOs” refers to the practice of learning and using programming languages and techniques to enhance Search Engine Optimization (SEO) efforts. SEO involves various strategies and tactics aimed at improving a website’s visibility in search engine results pages (SERPs). Programming skills can be extremely beneficial for SEO professionals as they enable them to implement technical optimizations, analyze data, and automate tasks. Here’s how programming can benefit SEOs:
1. Technical SEO Implementation: Programming skills allow SEOs to make technical changes to a website, such as optimizing meta tags, implementing structured data markup (Schema.org), creating XML sitemaps, and managing URL structures.
2. Website Speed Optimization: Programming knowledge is valuable for optimizing website performance, which is crucial for both user experience and SEO. Techniques like minification, caching, and lazy loading can be implemented using programming languages.
3. Web Crawling and Scraping: Programming allows SEOs to create custom web crawlers and scrapers to gather data from websites, analyze competitor websites, or extract information for research purposes.
4. Data Analysis and Visualization: Programming languages like Python can be used to analyze large datasets from sources like Google Analytics or search engine rankings. Visualization tools can be employed to present insights effectively.
5. Automation of Repetitive Tasks: Programming allows SEOs to automate routine tasks, such as generating reports, monitoring keyword rankings, and tracking backlinks, saving time and improving efficiency.
6. Custom SEO Tools: SEOs with programming skills can create custom tools tailored to their specific needs, helping them streamline their workflows and gain a competitive edge.
7. JavaScript SEO: With search engines becoming better at rendering JavaScript content, programming skills are valuable for implementing SEO strategies that involve client-side rendering and dynamic content.
8. Mobile-First Optimization: As mobile-friendliness is a critical SEO factor, programming skills are essential for optimizing websites for various screen sizes and devices.
9. Debugging and Troubleshooting: When technical issues arise on a website, SEOs with programming knowledge can effectively diagnose and resolve issues, minimizing disruptions to search rankings.
10. Knowledge of APIs: Many SEO tools offer APIs that allow customization and integration with other tools. Programming skills enable SEOs to harness the power of APIs for data retrieval and analysis.
Popular programming languages for SEOs include:
- Python: Widely used for web scraping, data analysis, and automation.
- JavaScript: Essential for front-end SEO and dynamic content optimization.
- PHP: Commonly used for server-side scripting and website development.
- SQL: Useful for managing and querying databases.
- R: Great for statistical analysis and data visualization.
While programming skills can greatly enhance an SEO professional’s capabilities, it’s important to note that not all SEOs need to be expert programmers. The level of programming proficiency required depends on the specific tasks and projects you’re working on.
PHP Form Validation
<?php
// define variables and set to empty values
$nameError = $emailError= $genderError = $websiteError = “”;
$name = $email = $gender = $comment = $website = “”;
if ($_SERVER[“REQUEST_METHOD”] == “POST”) {
if (empty($_POST[“name”])) {
$nameError = “Name is required”;
} else {
$name = test_input($_POST[“name”]);
// check if name only contains letters and whitespace
if (!preg_match(“/^[a-zA-Z ]*$/”,$name)) {
$nameError = “Only letters and white space allowed”;
}
}
if (empty($_POST[“email”])) {
$emailError = “Email is required”;
} else {
$email = test_input($_POST[“email”]);
// check if e-mail address syntax is valid
if (!preg_match(“/([\w\-]+\@[\w\-]+\.[\w\-]+)/”,$email)) {
$emailError = “Invalid email format”;
}
}
if (empty($_POST[“website”])) {
$website = “”;
} else {
$website = test_input($_POST[“website”]);
// check if URL address syntax is valid (this regular expression also allows dashes in the URL)
if (!preg_match(“/\b(?:(?:https?|ftp):\/\/|www\.)[-a-z0-9+&@#\/%?=~_|!:,.;]*[-a-z0-9+&@#\/%=~_|]/i”,$website)) {
$websiteError = “Invalid URL”;
}
}
if (empty($_POST[“comment”])) {
$comment = “”;
} else {
$comment = test_input($_POST[“comment”]);
}
if (empty($_POST[“gender”])) {
$genderError = “Gender is required”;
} else {
$gender = test_input($_POST[“gender”]);
}
}
function test_input($data) {
$data = trim($data);
$data = stripslashes($data);
$data = htmlspecialchars($data);
return $data;
}
?>
<h2>PHP Form Validation</h2>
<p><span class=”error”>* required field.</span></p>
<form method=”post” action=”<?php echo htmlspecialchars($_SERVER[“PHP_SELF”]);?>“>
Name: <input type=”text” name=”name”>
<span class=”error”>* <?php echo $nameError;?></span>
<br><br>
E-mail: <input type=”text” name=”email”>
<span class=”error”>* <?php echo $emailError;?></span>
<br><br>
Website: <input type=”text” name=”website”>
<span class=”error”><?php echo $websiteError;?></span>
<br><br>
Comment: <textarea name=”comment” rows=”5″ cols=”40″></textarea>
<br><br>
Gender:
<input type=”radio” name=”gender” value=”female”>Female
<input type=”radio” name=”gender” value=”male”>Male
<span class=”error”>* <?php echo $genderError;?></span>
<br><br>
<input type=”submit” name=”submit” value=”Submit”>
</form>
<?php
echo “<h2>Your Input:</h2>”;
echo $name;
echo “<br>”;
echo $email;
echo “<br>”;
echo $website;
echo “<br>”;
echo $comment;
echo “<br>”;
echo $gender;
?>
</body>
</html>
PHP Form Validation
* required field.
Your Input:
Name
Test@gmail.com
www.example.com
Test Comment
Female
Simple Capcha using php
Capcha Code:
Save this code as “capcha.php”
[php]
<?php
session_start();
$text = rand(10000,99999);
$_SESSION[“vercode”] = $text;
$height = 25;
$width = 65;
$image_p = imagecreate($width, $height);
$black = imagecolorallocate($image_p, 0, 0, 0);
$white = imagecolorallocate($image_p, 255, 255, 255);
$font_size = 14;
imagestring($image_p, $font_size, 5, 5, $text, $white);
imagejpeg($image_p, null, 80);
?>
[/php]
——————————————————————————————————
HTML:
<img src=”capcha.php” alt=”” align=”top” /> <input id=”vercode” class=”cap” name=”vercode” type=”text” align=”texttop” />
<div>
<input class=”sub” name=”subi” type=”submit” value=”Register” />
</div>
Must set session to use the capcha
PHP Code for the html page:
[php]
<?php if ($_POST[“vercode”] != $_SESSION[“vercode”])
{
header(“location:contact.php?ver”); //incorrect verification code }
?>
[/php]
PHP Sessions
Starting a PHP Session
- The session_start() function must appear BEFORE the <html> tag:
[php]
<?php session_start(); ?>
<html>
<body>
</body>
</html>
[/php]
- The above code is used to register the user session in server.
Destroying a Session
[php]
<?php
session_destroy();
?>
[/php]
- The above code is used to destroy the complete session from the server.
NOTE : The session is very very important to save the current user information on the server. Using UID(user id), The server saves the user information on the server.
Logos – Unknown Facts
Logos are not only meant for design.As a end user one can view the logo’s look and feel.But the designers should know the hidden meaning behind it.
View some of them here.
Can you find the symbol which is hidden in the Federal Express logo? Look at the logo. You can see the ‘arrow’ between the E and X in this logo.The arrow was to highlight swiftness and accuracy, which are part of the positioning of the company.
Paul Rand designed the iconic IBM logo in the year 1972.Later on 1981 he designed this ‘eye bee M’ logo. Actually IBM stands for “International Business Machines”.
An amazing instance of symmetry and order is the SUN Microsystems logo. When you observe the logo, the letters u and n while arranged adjacent to each other look a lot like the letter S in a perpendicular direction.
Have a look at the arrow in the logo. You may imagine that the arrow does nothing here. But it convey a message that amazon.com has everything from a to z and it also represents the smile brought to the customer’s face.
Programmers Reaction
See the reactions of an ordinary man and a programmer while in danger.
Ordinary Man
Programmer
Definition of Open Source
The term “Open source” does not just represent right to use the source code. The distribution terms of open-source software has a necessity to meet the terms with the subsequent standards:
- Redeployment without charge
- Source Code
- Derived Works
- Reliability of the Author’s Source Code
- No inequity against Persons or Groups
- No favoritism against Fields of Endeavor
- Distribution of License
- License should Not Be precise to a Product
- License Must Not Restrict Other Software
- License Must Be Technology-Neutral
The certificate does not limit anyone from advertising or giving away the software as a module of a combined software distribution encloses programs from numerous different sources. The license does not entail a fee or other payment for such sale.
The program should consist of source code. It has to permit sharing of source code in compiled form. If some form of a product is not circulated with source code, there must be a fine revealed means of how to obtain the source code for a rational reproduction cost preferably, downloading via the Internet without charge. The format of source code must be like a programmer can be able to alter the program. Intermediate forms like output of a preprocessor or translator are not permitted.
The warrant must let them to make any modifications and derived works. It should permit them to be distributed the software under the similar conditions as the license of the original software.
The license possibly will confine source-code from being distributed in customized form only if the license agrees to distribute “patch files” with the source code for the intention of transforming the program at build time. The license must openly allow distribution of software built from modified source code. The license may need derived works to bring out different name or version number from the original software.
The license is required to distinguish beside any person or group of persons.
The license should not put a ceiling on making use of the program in a particular field of endeavor. For instance, it may not confine the program from being used in a trade, or from being used for genetic observations.
The rights enclosed to the program should be relevant to all to whom the program is rearranged with no need for implementation of an additional license by those parties.
The rights attached to the program should be unique. It should not depend on other program’s which is part of a particular software distribution.
The authorization should not put limitations on other software that is distributed in conjunction with the licensed software. For instance, the license should not claim that all other programs distributed on the similar medium ought to be open-source software.
No stipulation of the license may be predicated on any individual technology or style of interface.
Are you a real programmer? How can you tell that?
This is really amusing for one and all to read.
Machine code is your pseudo code
You trust that by means of a linker or a macro library to make a program is “dirty”, a real programmer does not get baffled when the source code get to 6000 lines in one file
You suppose that PC playoffs are a squander of CPU cycles.
While you are at a monetary firm coding for mainframes in mainframe assembly (the manager inform him to code in Assembly rather than machine code so the other ‘normal’ programmers may possibly be aware of what is going on)
You construct your individual programming languages and provide them crappy names.
You were not being fond of multicore systems. You accept as true that if you cannot formulate a program to run fast enough on a single core, you are not a programmer.
You will never utilize operating system interrupts … you make your own.
If your random number generator creates the random numbers from zero to infinity in 5 seconds, you believe it as very slow.
You consider that remarking the source code is for the amateur.
You don’t make use of computers outside of work. You will not have belief on other programmer’s code.
You judge that technologies like PHP, Python or VBA were not a programming language- it is only scripting language.
You don’t want to use Object Orientation for the reason that it makes your work trouble-free. In any case you wish for a challenge.
C++ and APL programming languages was a toy to you.
Someone point out the languages like VB and JAVA to you, you will give a punch them on the head.
Even if your code has been typed up, it was already optimized.
You get clear of the Back Space key on the Keyboard as you do not make any mistakes.
You don’t like to have any book or notepads; it’s all in your head.
Your programs are not user friendly, even if they are bug free.
You have a nightmare of creating your own CPU for yourself one day and maintain it in your parent’s garage.
You thought that IDE’s, Programmer Tools and Syntax Highlighters are for people who do not be familiar with what they are doing.
You return back the computer mouse to the technician, with a screw driver stabbed through it. Real programmers will make use of command prompt only.
If the client does not be fond of what you perform for them, you think that the client is an idiot and you say “No” to alter anything.
Who wants friends when you can program your own friends.